Earlier today at 11:24 The Guardian Journalist Shaun Walker posted the security procedure and the security token used to pass makeshift checkpoints in Ukraine related to the Russian Ukrainian war:
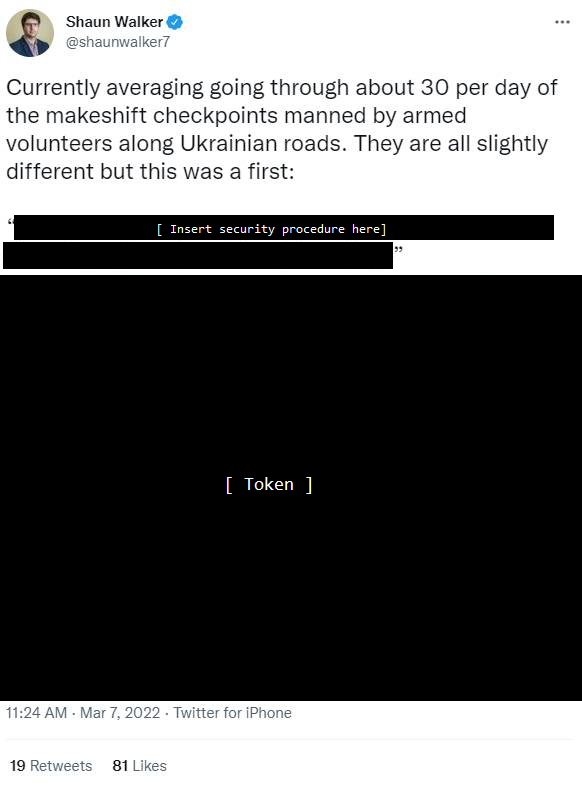
This is a reminder to journalists – and the public – to take OPSEC (operations security) seriously and not endanger people on the ground.
Posting a security token – whether digital (cookies, passwords, keys) or physical is endangering the people this very security token tries to protect.
Above tweet was also posted on the current live ticker about the Russian Ukraine war on theguardian.com (it has been removed since).
Mistakes can happen. Mr. Walker deleted the post after many Twitter users pointed out the mistake. However, there is a lack of accountability. Mr. Walker writes:
The problem with the statement “how posting this without location compromises security” is the same as when people declare “it is just an XSS vulnerability”. In real world attacks, vulnerabilities (and password/information disclosures) are often used in connection (chained) with other vulnerabilities to form an actual attack.
In this particular case other tweets could reveal the location, or perhaps the posted picture could reveal the geo-location via EXIF data. Public reports already revealed that some Russian soldiers (saboteurs) pretend to be Ukrainian ones including the use of their uniform and vehicles.
Revealing the security details and tokens of checkpoints of an active warzone is certainly not smart, has little journalistic value (if any at all) and The Guardian should know better.