Can we DDoS ourselves? We are about to find out. Live self-ddos on 10.05.2020 13:00 UTC
On Sunday, May 10, 2020, we will DDoS our own website, intelx.io. We will live tweet and update this blog post with any developments and the outcome. The attack will be executed in the same fashion as an actual attack: we’ll do some research, then pay a shady DDoS provider in Bitcoin (and hope they don’t scam us) and launch an actual DDoS attack against our own website.
https://twitter.com/_IntelligenceX/status/1259103590427303936
Note: We own 100% of our infrastructure including the servers, network equipment, and even our own BGP router. We are our own ISP and operate our own Autonomous System and IP addresses. We do not recommend anyone to launch DDoS attacks.
Step 1: Find a DDoS Provider
The first step is to find an actual DDoS provider. They are often advertised on hacking forums and can be found via search engines.
There is a recent blog post here discussing law enforcement actions against DDoS providers.
SynStresser.com
Accessible via synstresser.to and synstresser.com, it claims to support “Layer 3, Layer 4, and Layer 7 DDos methods”. It claims to bypass multiple DDoS-protection providers, including “Cloudflare on all its modes, Blazingfast, CyberDDOS, Sucuri WAF, and almost all other DDOS protections”.
The Telegram account, “jeffspender”, is linked in the footer as the contact person. There is a YouTube channel youtube.com/watch?v=6naFV90FaU8 which joined in October 31, 2018.
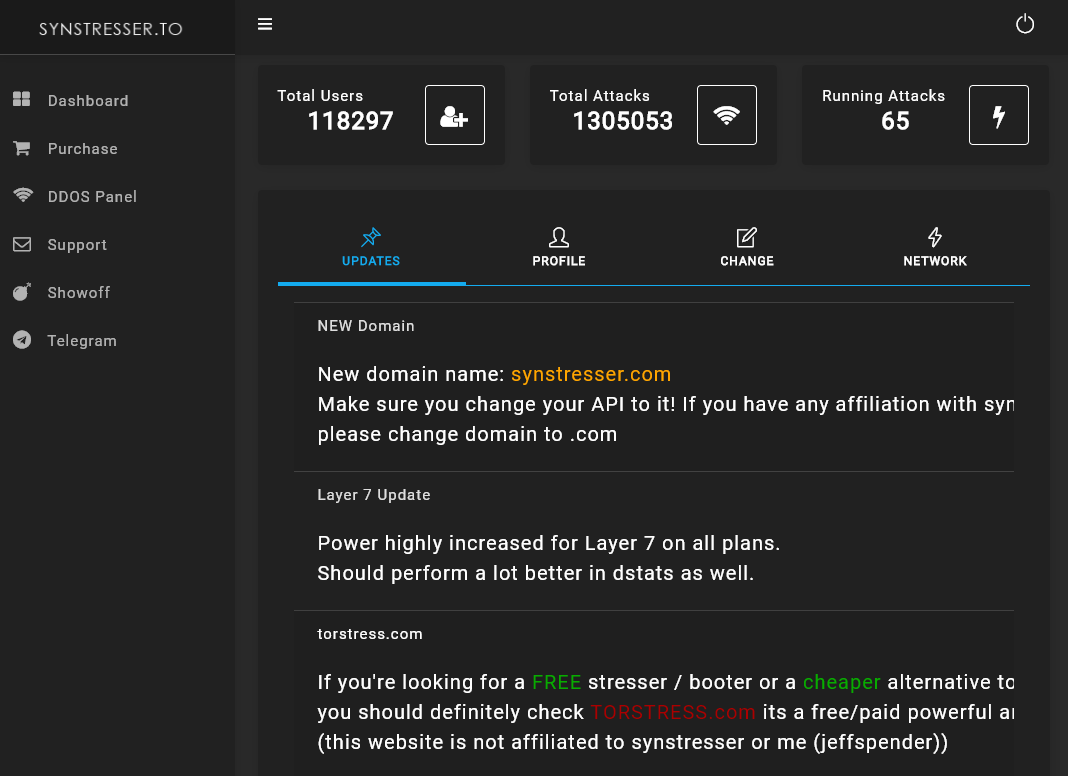
The pricing starts at €50 for 10 minutes. 3 hours cost €135. There are multiple upgrades, including the option to launch “concurrent attacks” (which does not make much sense since DDoS attacks are already distributed by nature; i.e., concurrent attacks from many machines) as well as “Premium +€150” and “Enterprise +€300” “attack network” options.
Here is a GIF ad:

According to our whois data at intelx.io/?did=95636af6-f7b0-4240-9615-10aa031747b4, the domain synstresser.com was registered on 2019-12-04 via the Chinese registrar todaynic.com.
torstress.com
Another one is torstress.com. It lists the Telegram contacts “torstress” and “xCrucial”.
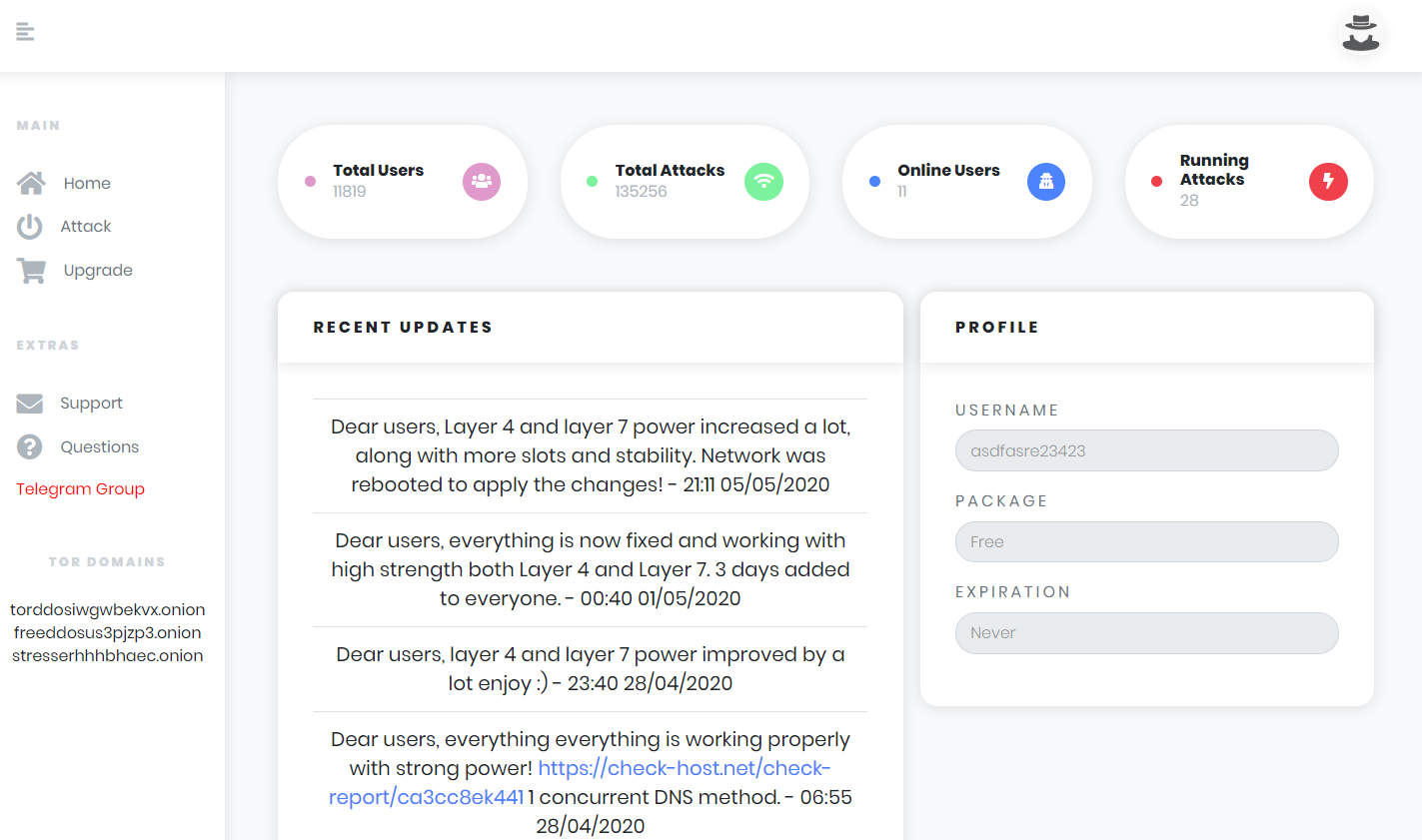
There is a free tier, but it does not mention how strong the free attack is. The paid packages start at $15 per month for “1200 seconds per attack” and go up to $500 per month for “10800 seconds per attack”.
torstress.com was registered on 2020-03-22 via the Chinese registrar todaynic.com.
Others
The website slayer.st lists a bunch of others. Note that no DDoS service here was vetted and they may or may not be scams. Most of them offer a free trial (like launching the attack for 60 seconds), which is good enough for the use case here.
- databooter.to
- asylumstresser.to
- freestresser.to – offers a free “1Gbps spoofed UDP floods”
- nightmarestresser.to
- layer7-security.to
- stressthem.to
- stresser.wtf
- instant-stresser.com
- undisclosed.to
- quez.in
- freeboot.to
- packets.world
- minesearch.rip
- meteor-security.to
- instress.me
- stress.to
- ipstresser.com
- str3ssed.co
Step 2: Signup
Signup is easy as the DDoS services often don’t even require an email address.
Step 3: Launch the attack
We have first tested targeting our network equipment with ddos services that offer free attacks.
Test 1: “databooter.to”. This resulted in a very small attack in Kbit traffic (which is not even worth mentioning) and single digit source IPs.
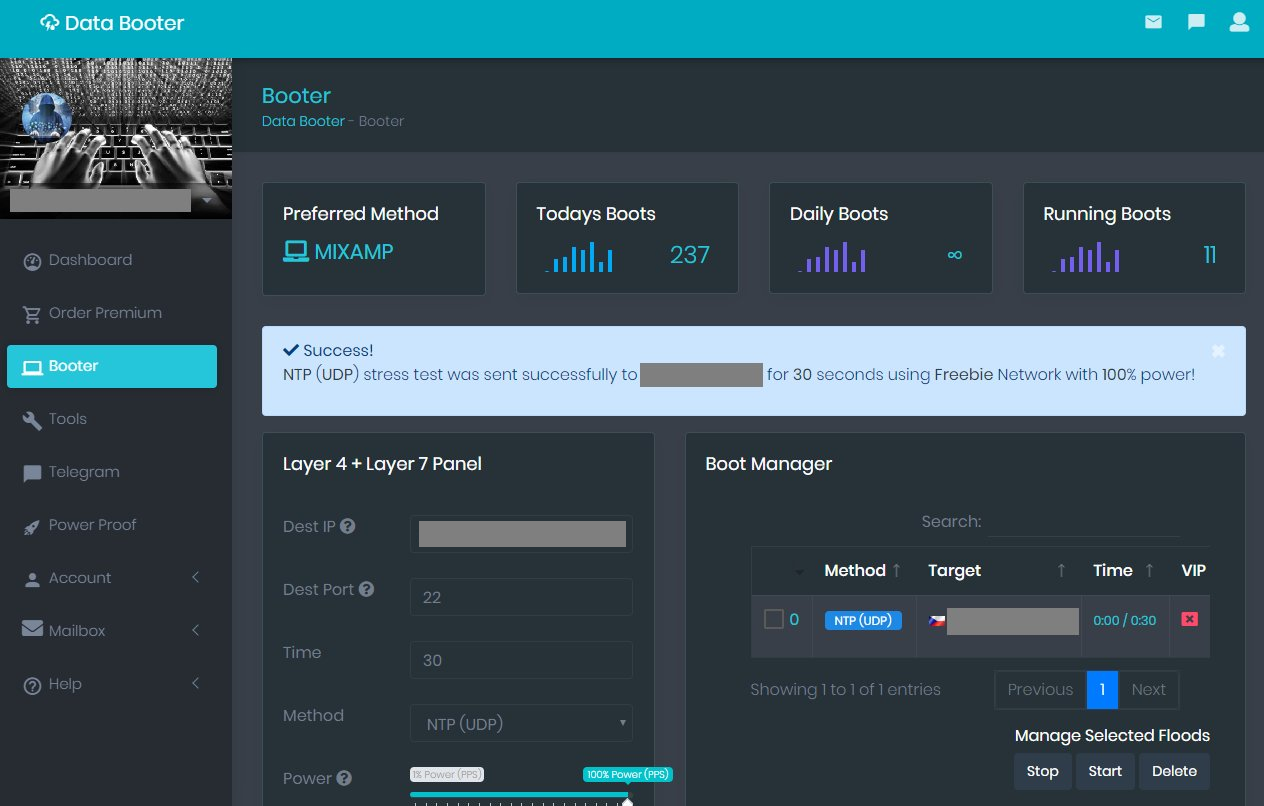
Test 2: stressthem.to. The attack (free tier) reaches 1 Gbit. Our switch remained operational though, only 15% CPU spike and no practical impact.

Test 3: torstress.com. The user interface is a but biggy, but the service does the job. We measured more than 150,000 packets per second which is decent, especially as it’s free.
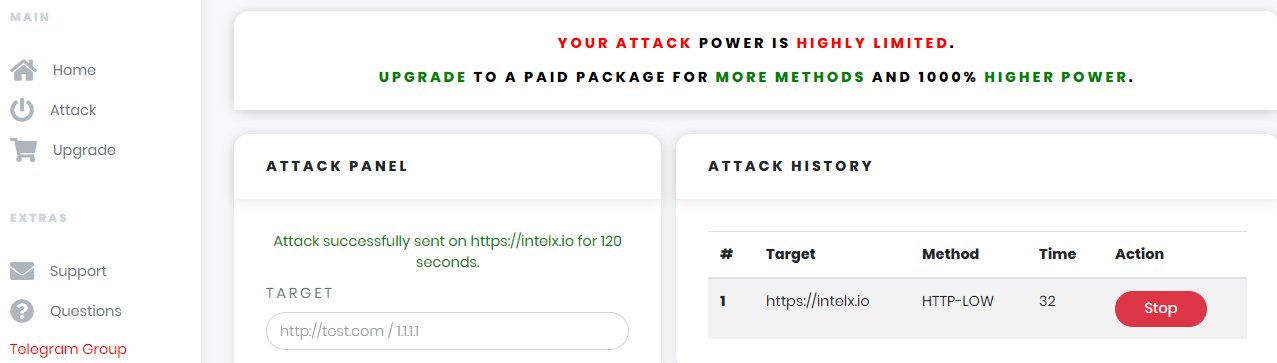
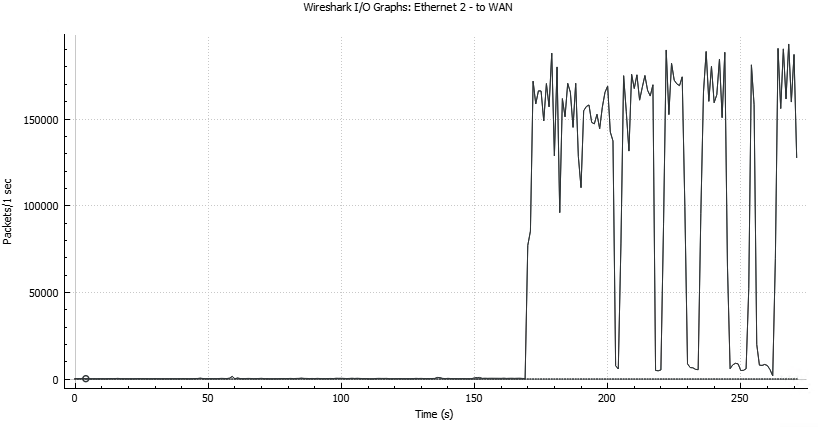
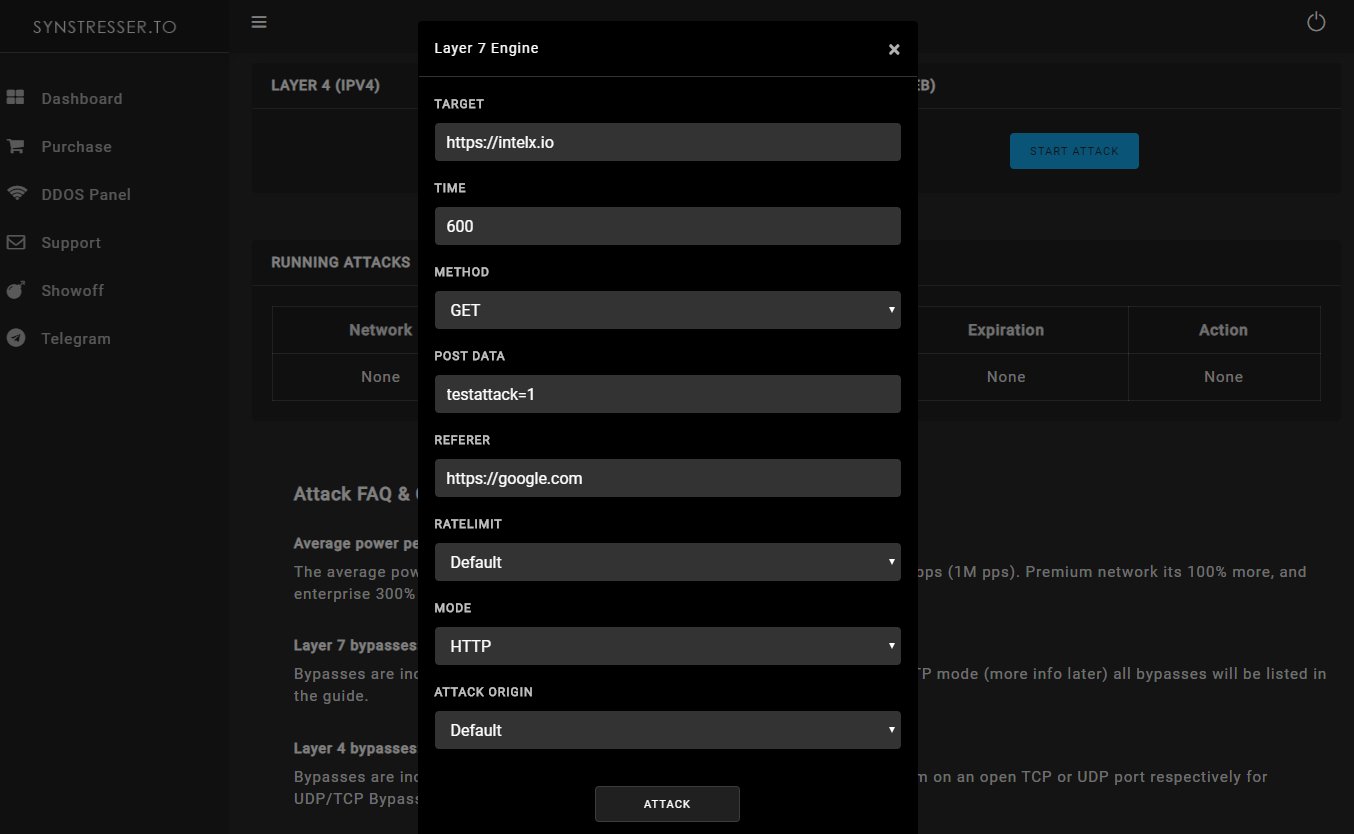
Live attack: We are using synstresser.com for the actual live attack. We launched a bunch of different attacks over the course of 2 hours.
A first initial one using HTTP for 60 seconds was not successful. Only 730 requests arrived at our server – the full log is here pastebin.com/GS2nE2U1. A later attack with HTTP resulted in more than 10,000 requests which still had not significant impact.
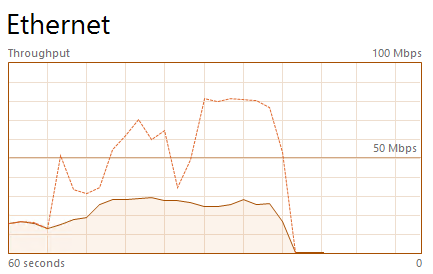
We tested other DDOS modes including “TCP-SSYN” which launches a TCP-SYN attack. It was able to slow down incoming connections, but did not result in a complete denial of service.
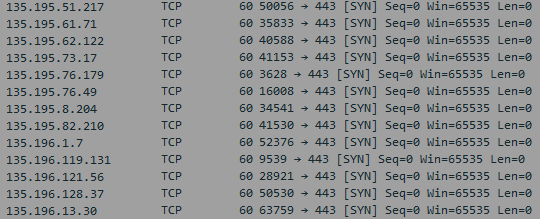
This attack resulted in over 2.5 million unique IPs sending 7 million packets in 1 minute. The IP addresses are potentially spoofed.

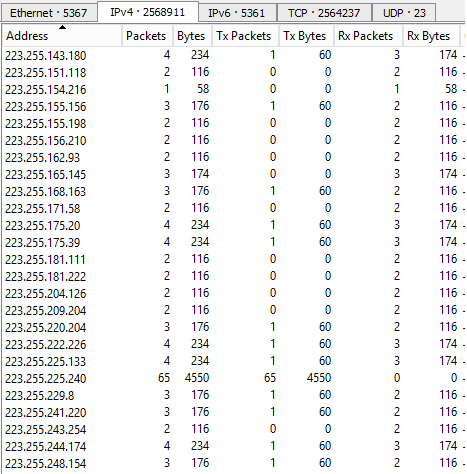
Measuring the impact
The impact can be measured in numerous ways. The most obvious one: is the site accessible? Does the attack have a lasting impact?
On a technical level, there are many questions that boil down to “how big is the attack?”:
- How many unique IPs are used? Are they possibly spoofed?
- What protocol is used? ICMP/UDP/TCP etc.
- Is it a low-level attack (flooding) or an application-level denial-of-service attempt?
- How many packets/requests in total? How many per second?
- What are the characteristics of the DDos software? Does it rotate or randomize certain TCP or HTTP fields?
Since we are our own attacker, some of them (like the type of attack) can be obviously influenced by ourselves. Still, it makes sense to record the attack and verify.
Takeaways
- Some attacks have no impact at all
- Network level attacks (TCP SYN, NTP, DNS) can often be filtered and mitigated via simple firewall rules
- Some of the attacks are successful in slowing down the responsiveness of the website
No attack had any permanent effect.