On December 11, 2019 we have received 31,866 HTTP requests from the IP 81.171.107.57. Below are few sample log entries:
81.171.107.57 - - [11/Dec/2019:13:52:37 +0000] "POST /login HTTP/1.1" 200 7448 81.171.107.57 - - [11/Dec/2019:13:52:37 +0000] "POST /login HTTP/1.1" 200 7443 81.171.107.57 - - [11/Dec/2019:13:52:37 +0000] "POST /login HTTP/1.1" 200 7447 81.171.107.57 - - [11/Dec/2019:13:52:37 +0000] "POST /login HTTP/1.1" 200 7484 81.171.107.57 - - [11/Dec/2019:13:52:37 +0000] "POST /login HTTP/1.1" 200 7481
This IP address logged into intelx.io with the email address “testeur.1@live.fr” on 11.12.2019 13:44:59. The IP address space 81.171.107.0/24 is owned by https://privado.io/ – a VPN provider.
However, 30 seconds earlier, the same user logged in with the IP 90.118.11.30. That IP address belongs to the telecom provider Orange:
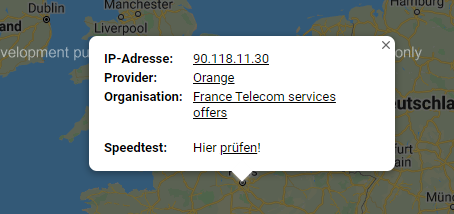
The account testeur.1@live.fr signed up at intelx.io on 2019-12-11 13:29:41 using the IPv6 2a01:cb1c:3e7:d500:2cbc:202:4e89:793b, which is also owned by Orange France.
Of course we would use our own search engine to find information about the attacker: https://intelx.io/?s=testeur.1@live.fr
The first result shows a SQL record at the hacking forum cracked.to:
INSERT INTO `mybb_users` VALUES ('234852', 'ericpompier', '$2y$12$OwDnC91.sCimfleGaHDzK.7VzqCrSaOPcaH.z2kWvr8jZJ8jHGqEq', 'eWwwAciL', 'MVdK6y3YfPeqyvBYQ08GZmwof3sQs6XIOs6egfuUlKxJtMqFyg', 'testeur.1@live.fr', '7', '0', '', '', '', '2', '', '0', '', '1560073804', '1561582600', '1560964307', '1561582563', '', '0', '', '', '', '', '', 'all', '', '1', '0', '0', '0', '1', '0', '1', '0', '1', '0', 'linear', '1', '1', '1', '1', '1', '1', '0', '0', '0', '', '', '', '0', '0', '', '', '0', '0', '0', '0', '', '', '', '0', '0', '0', 0x2A01CB1C03D0C8004CBB659841E0FE70, 0x2A01CB1C03D0C800417A4418025C83E0, '', '1716', '1', '0', '0', '0', '0', '0', '0', '0', '0', '0', '0', '1', '1', '0', '', '0', '0.00', '1', '0', '0', '0', '', '1', '1', '2', '0', '0', '0', '0', '[]', '1', null, null, null, '1', '', '', '0', '0', '0', '', '', '', '', '', '0', '', '', '', '0', '0', '0', '1', '0', '0', '0', '6', '0', '0', '0', '', '0', '', '0', '0', '0', '', '', '', '', '', '', '', '', '', '', '0', '', 'mybb_bcrypt', '0', '');
It reveals the username “ericpompier”. https://cracked.to/ericpompier shows the user signed up on 09 June, 2019 and wrote 12 posts – mostly saying “thank you” to unlock the OPs (original posters) “hidden links”:
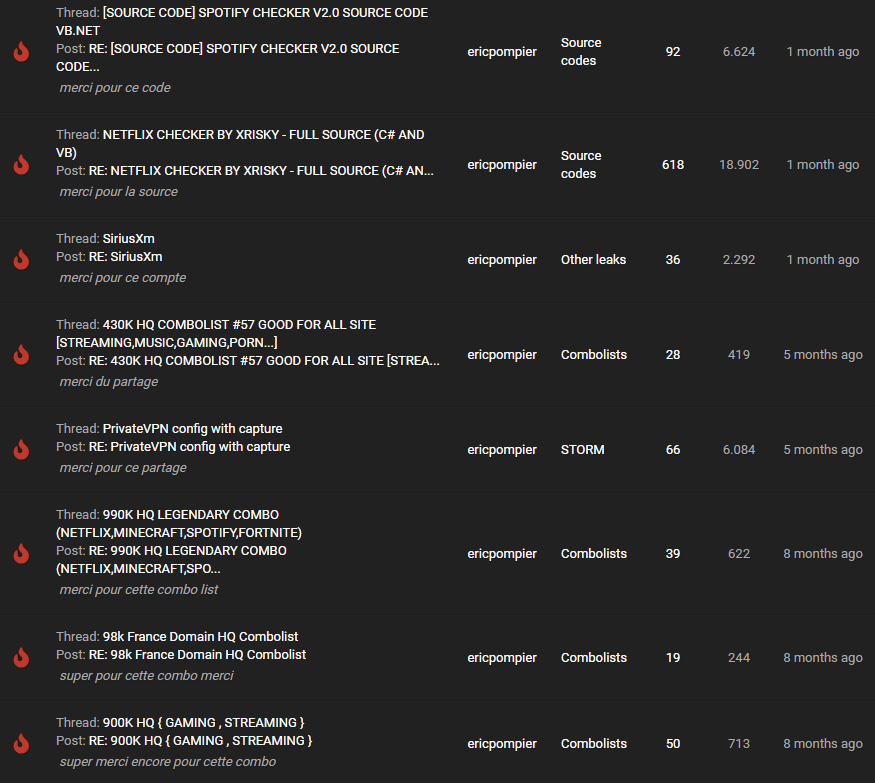
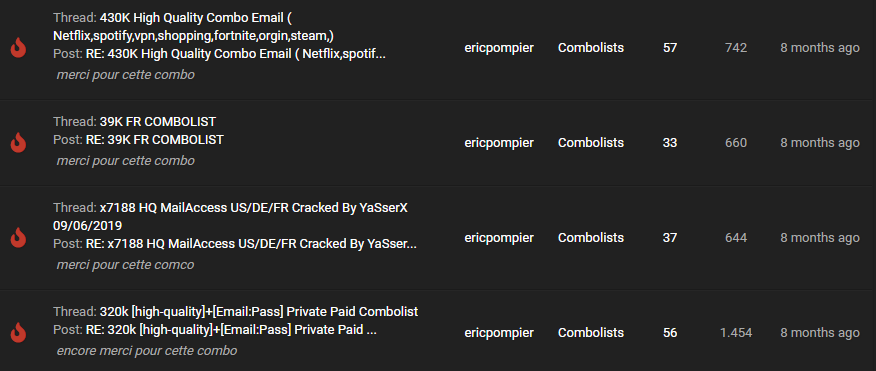
Another search result reveals a SQL record of the DemonForums.net hacking forum. It reveals the same username “ericpompier”.
INSERT INTO mybb_users (`uid`,`username`,`password`,`salt`,`loginkey`,`email`,`postnum`,`awards`,`threadnum`,`avatar`,`avatardimensions`,`avatartype`,`usergroup`,`additionalgroups`,`displaygroup`,`usertitle`,`regdate`,`lastactive`,`lastvisit`,`lastpost`,`website`,`icq`,`aim`,`yahoo`,`skype`,`google`,`birthday`,`birthdayprivacy`,`signature`,`allownotices`,`hideemail`,`subscriptionmethod`,`invisible`,`receivepms`,`receivefrombuddy`,`pmnotice`,`pmnotify`,`buddyrequestspm`,`buddyrequestsauto`,`threadmode`,`showimages`,`showvideos`,`showsigs`,`showavatars`,`showquickreply`,`showredirect`,`ppp`,`tpp`,`daysprune`,`dateformat`,`timeformat`,`timezone`,`dst`,`dstcorrection`,`buddylist`,`ignorelist`,`style`,`away`,`awaydate`,`returndate`,`awayreason`,`pmfolders`,`notepad`,`referrer`,`referrals`,`reputation`,`regip`,`lastip`,`language`,`timeonline`,`showcodebuttons`,`totalpms`,`unreadpms`,`warningpoints`,`moderateposts`,`moderationtime`,`suspendposting`,`suspensiontime`,`suspendsignature`,`suspendsigtime`,`coppauser`,`classicpostbit`,`loginattempts`,`usernotes`,`sourceeditor`,`passwordconvert`,`passwordconverttype`,`passwordconvertsalt`,`tyl_unumtyls`,`tyl_unumrcvtyls`,`tyl_unumptyls`,`newpoints`,`memberstatus`,`ts_uids`,`theme_h`,`theme_s`,`theme_b`,`vouches`,`sidebarinvisible`,`sidebarforums`,`twostepauth_enabled`,`twostepauth_hide_hint`,`twostepauth_method`,`thx`,`thxcount`,`thxpost`,`thx_ammount`,`thx_antiflood`,`profilebg`,`rep_alert`,`quote_alert`,`reply_alert`,`mention_alert`,`like_alert`,`rps_played`,`rps_profit`,`rps_totalwagered`,`rps_wins`,`rps_losses`,`rps_ties`,`passwordupdated`,`tooltipenabled`,`changelocation`,`2facode`,`showawards`,`showsidebar`,`fixedheader`,`profile_visits`,`showvisitors`,`colour`,`shadow`,`myprofilecomments_num`,`rankid`,`nextrankid`,`postbitcover`,`theme_hexcolor`,`ytvideoid`,`secret`,`themehex`,`earlier_bans`,`postbit_background`,`postbit_background_opacity`,`forcepwchange`) VALUES ('10643','ericpompier','cad897f56807a84783066e897f9caf31','vykM8j47','qA3lhwzKQAJl2f3WumZzO6R2sbABQKTAlO6IS5qX9cY8Rhdzcf','testeur.1@live.fr','0','0','0','./images/df/default_avatar.png','','','2','','0','','1476865254','1476865334','1476865254','0','','0','','','','','','all','','1','0','0','0','1','0','1','0','1','0','linear','1','1','1','1','1','1','0','0','0','','','0','0','2','','','84','0','0','0','','','','0','0','0','ZI ','ZI ','','80','1','0','0','0','0','0','0','0','0','0','0','1','17','','0',NULL,NULL,NULL,'0','0','0','0.00','0','','0','100','100','0','1',NULL,'0','0','1','0','0','0','0','0','','1','1','1','1','1','0','0','0','0','0','0','0','1','Secret','0','1','1','1','0','1','','','0','0','2',NULL,'c84040','N/A','','#c84040','0',NULL,NULL,'0');
It is worth noting that we are fully compliant with privacy laws as well as our own privacy policy. When signing up, the user “testeur.1@live.fr” agreed that information about attacks may be collected and shared with the public and law enforcement.
Intelligence X will continue to publish information about attacks affecting our company and service.