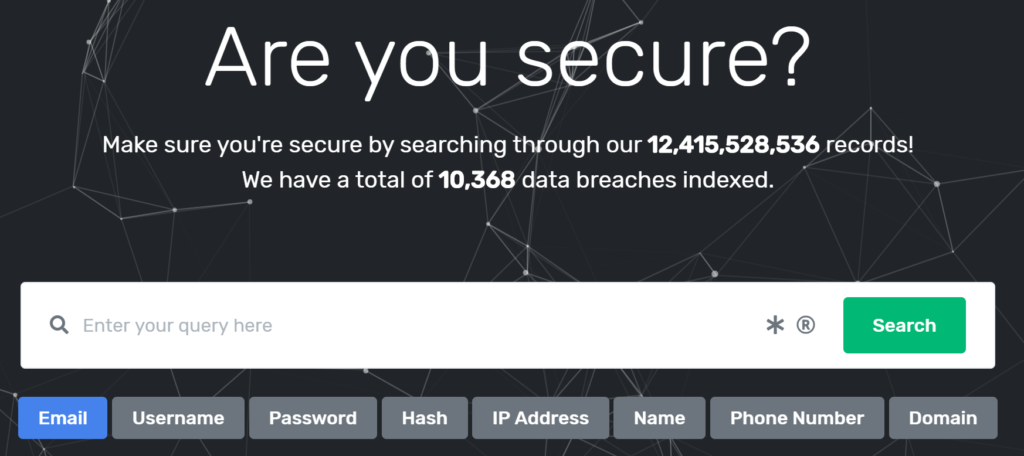
The domain weleakinfo.com was seized yesterday by the FBI. The website shows a takedown notice and shows the logos of NCA, Politie, Police Service Northern Ireland, Department of Justice and Bundeskriminalamt. The note writes:
This domain has been seized
The domain for WELEAKINFO has been seized by the Federal Bureau of Investigation pursuant to a seizure warrant issued by the United States District Court for the District of Columbia under the authority of 18 U.S.C. §§ 981, 982, inter alia, as part of coordinated law enforcement action by: [logos]
The FBI released – hours after the takedown notice appeared, and users questioned its legitimacy – a press statement here https://www.justice.gov/usao-dc/pr/weleakinfocom-domain-name-seized:
FOR IMMEDIATE RELEASE
Thursday, January 16, 2020
WeLeakInfo.com Domain Name Seized
Site Had Sold Access to Hacked Personal Information and Account Logins
WASHINGTON – Today, the Federal Bureau of Investigation and the U.S. Department of Justice announced that they have seized the internet domain name weleakinfo.com. The announcement was made by U.S. Attorney Jessie K. Liu of the District of Columbia and Special Agent in Charge Timothy M. Dunham of the FBI’s Washington Field Office.
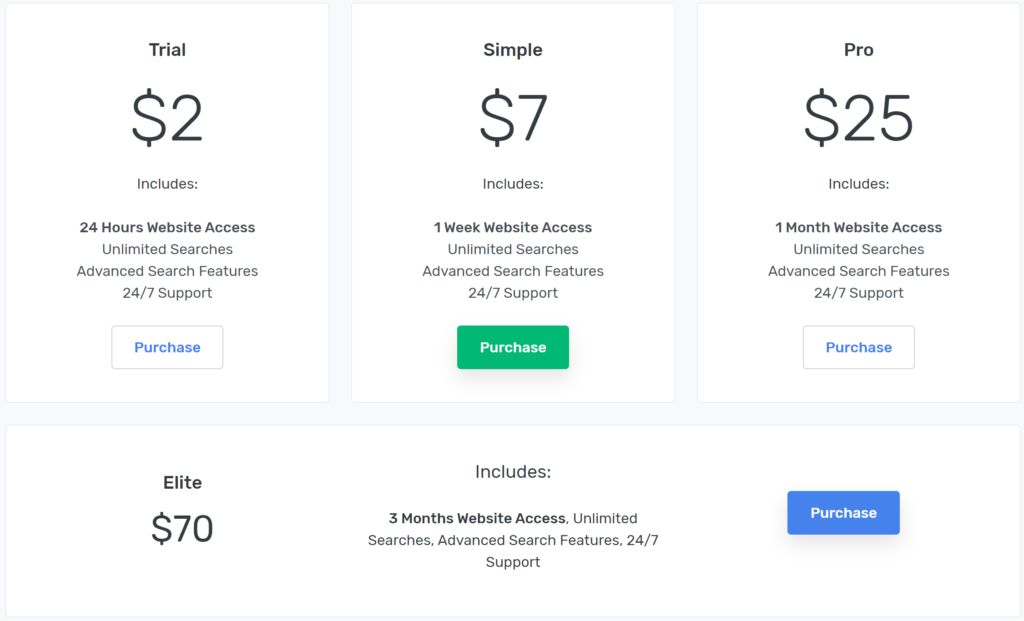
The website had claimed to provide its users a search engine to review and obtain the personal information illegally obtained in over 10,000 data breaches containing over 12 billion indexed records – including, for example, names, email addresses, usernames, phone numbers, and passwords for online accounts. The website sold subscriptions so that any user could access the results of these data breaches, with subscriptions providing unlimited searches and access during the subscription period (one day, one week, one month, or three months).
With execution of the warrant, the seized domain name – weleakinfo.com – is now in the custody of the federal government, effectively suspending the website’s operation. Visitors to the site will now find a seizure banner that notifies them that the domain name has been seized by federal authorities. The U.S. District Court for the District of Columbia issued the seizure warrant.
Any persons having information concerning weleakinfo.com or its owners and operators are encouraged to provide that information by filing a complaint (referencing #weleakinfo in the “Description of Incident” field) with the FBI’s Internet Crime Complaint Center (IC3) at https://www.ic3.gov/complaint/default.aspx.
The seizure is part of a comprehensive law enforcement action taken by the FBI, the U.S. Attorney’s Office for the District of Columbia, and the Department of Justice’s Computer Crime and Intellectual Property Section, along with international law enforcement, including the United Kingdom’s National Crime Agency, the Netherlands National Police Corps, the German Bundeskriminalamt (the Federal Criminal Police Office of Germany), and the Police Service of Northern Ireland.
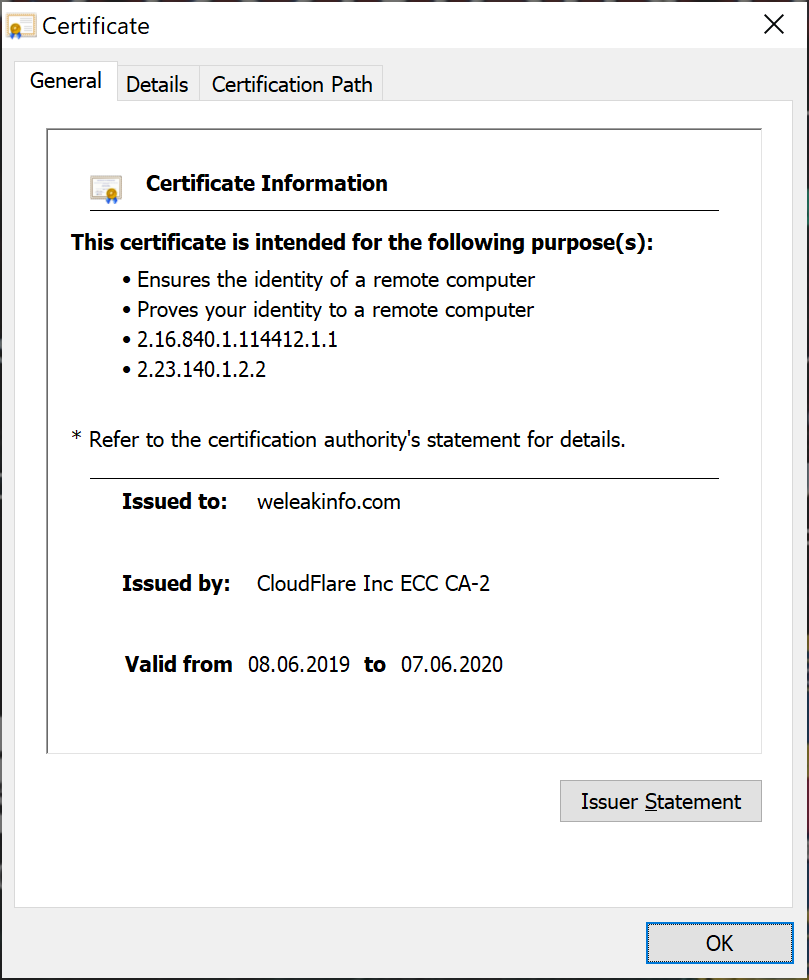
It looks like the FBI took over control of the domain by simply asking CloudFlare, who was the immediate hoster of the website. The current SSL certificate was issued by “CloudFlare Inc ECC CA-2” and is valid from 08.06.2019 until 07.06.2020 – indicating that the FBI took control of either the server, the CloudFlare account, or both.
The whois information appears to be unchanged and shows privacy protected information. However, it reveals that it was registered on 2016-08-24.
Domain Name: WELEAKINFO.COM
Registry Domain ID: 2054791391_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.dynadot.com
Registrar URL: http://www.dynadot.com
Updated Date: 2019-08-08T09:12:26.0Z
Creation Date: 2016-08-24T12:45:36.0Z
Registrar Registration Expiration Date: 2021-08-24T12:45:36.0Z
Registrar: DYNADOT LLC
Registrar IANA ID: 472
Registrar Abuse Contact Email: abuse@dynadot.com
Registrar Abuse Contact Phone: +1.6502620100
Domain Status: clientTransferProhibited
Registry Registrant ID:
Registrant Name: We Leak Info c/o Dynadot
Registrant Street: PO Box 701
Registrant Street:
Registrant City: San Mateo
Registrant State/Province: California
Registrant Postal Code: 94401
Registrant Country: US
Registrant Phone: +1.6505854708
Registrant Email: weleakinfo.com@superprivacyservice.com
Registry Admin ID:
Admin Name: We Leak Info c/o Dynadot
Admin Street: PO Box 701
Admin Street:
Admin City: San Mateo
Admin State/Province: California
Admin Postal Code: 94401
Admin Country: US
Admin Phone: +1.6505854708
Admin Email: weleakinfo.com@superprivacyservice.com
Registry Tech ID:
Tech Name: We Leak Info c/o Dynadot
Tech Street: PO Box 701
Tech Street:
Tech City: San Mateo
Tech State/Province: California
Tech Postal Code: 94401
Tech Country: US
Tech Phone: +1.6505854708
Tech Email: weleakinfo.com@superprivacyservice.com
Name Server: ns1.weleakinfo.com
Name Server: ns2.weleakinfo.com
DNSSEC: signedDelegation
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
Last update of WHOIS database: 2020-01-16 21:25:03 -0800
Hours before the takedown, the Twitter account @weleakinfo posted:
According to a recent Web Archive copy, it offered these subscription:
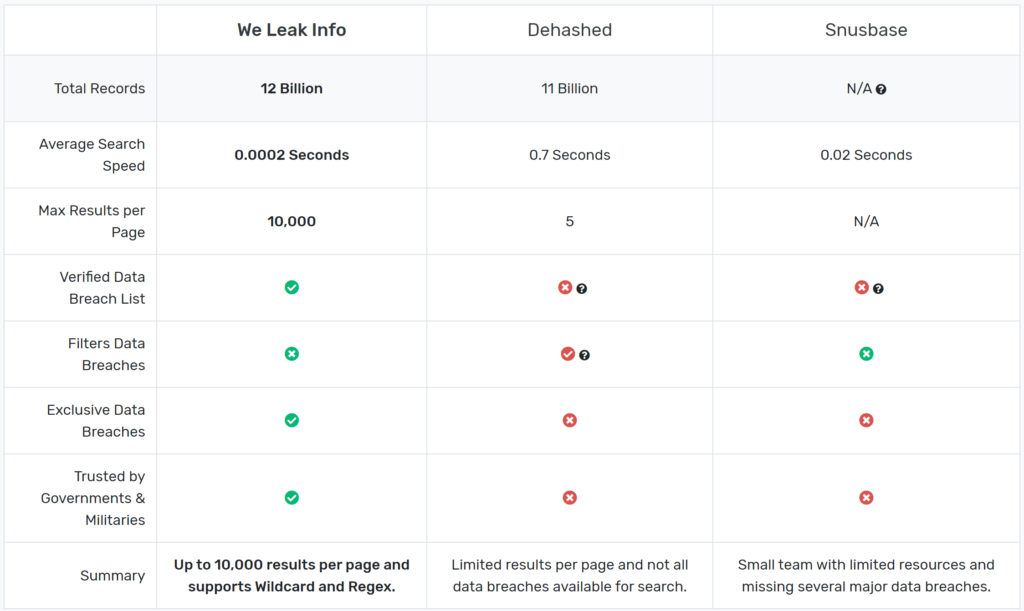
The website listed a comparison to the similar services “dehashed” and “snusbase”:
That is the million dollar question and the FBI wants you to inform them, in case you know it. The press release stated “Any persons having information concerning weleakinfo.com or its owners and operators are encouraged to provide that information by filing a complaint”.
The Terms of Service and Privacy Policy did not identify the owners or operators.
The only known associated email address is admin@weleakinfo.com. It appeared in the API documentation, the support page and on Twitter.
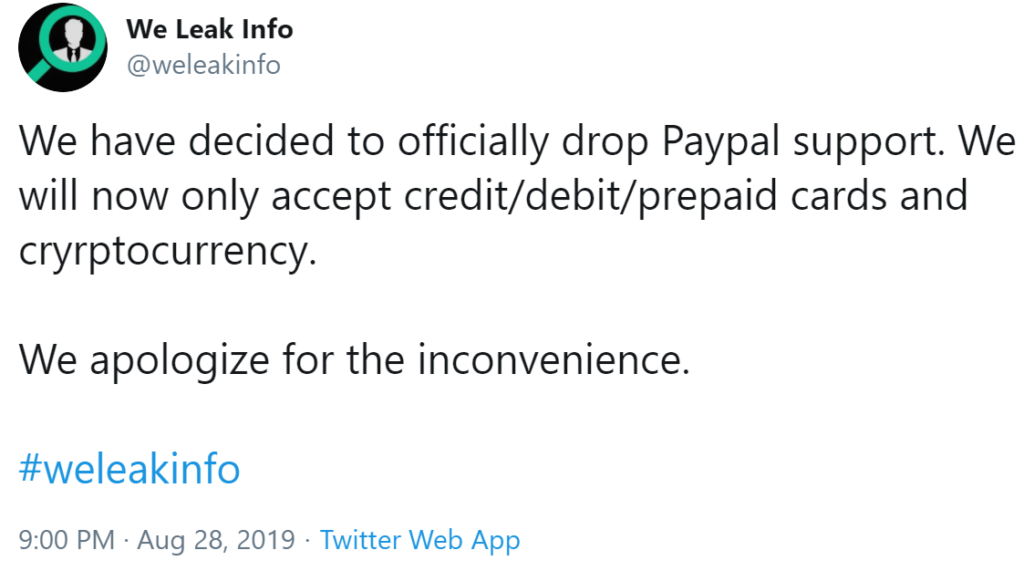
Other than following the hosting infrastructure, investigators could simply follow the money. According to https://twitter.com/weleakinfo/status/1166787572795940865, it accepted at one point PayPal, as well as credit/debit/prepaid cards and cryptocurrency:
They have 317 certificates according crt.sh. Some of them were issued by Let’s Encrypt, which asks optionally for an email address. weleakinfo was using Cloudflare since its early days (at least 2016-08-29) as provider.
SecurityTrails lists 19 subdomains, which provide additional points for investigations:
| # | Domain | Alexa Rank | Hosting Provider | Mail Provider |
|---|---|---|---|---|
| 1 | weleakinfo.com | 106,104 | Cloudflare, Inc. | NeuStar, Inc. |
| 2 | search.weleakinfo.com | ‐ | Cloudflare, Inc. | ‐ |
| 3 | chargebee.weleakinfo.com | ‐ | ‐ | ‐ |
| 4 | www.weleakinfo.com | ‐ | Cloudflare, Inc. | ‐ |
| 5 | ns2.weleakinfo.com | ‐ | Cloudflare, Inc. | ‐ |
| 6 | verizon.weleakinfo.com | ‐ | ‐ | ‐ |
| 7 | docs.weleakinfo.com | ‐ | Google LLC | ‐ |
| 8 | ns1.weleakinfo.com | ‐ | Cloudflare, Inc. | ‐ |
| 9 | akamai.weleakinfo.com | ‐ | ‐ | ‐ |
| 10 | blog.weleakinfo.com | ‐ | Cloudflare, Inc. | ‐ |
| 11 | api.weleakinfo.com | ‐ | Cloudflare, Inc. | ‐ |
| 12 | status.weleakinfo.com | ‐ | Amazon.com, Inc. | ‐ |
| 13 | staging.weleakinfo.com | ‐ | Cloudflare, Inc. | ‐ |
| 14 | beta.weleakinfo.com | ‐ | ‐ | ‐ |
| 15 | tracking.mail.weleakinfo.com | ‐ | Amazon.com, Inc. | ‐ |
| 16 | support.weleakinfo.com | ‐ | Cloudflare, Inc. | ‐ |
| 17 | updates.weleakinfo.com | ‐ | Fastly | ‐ |
| 18 | unauthorized.weleakinfo.com | ‐ | ‐ | ‐ |
| 19 | crisp.weleakinfo.com | – | DigitalOcean, LLC | – |
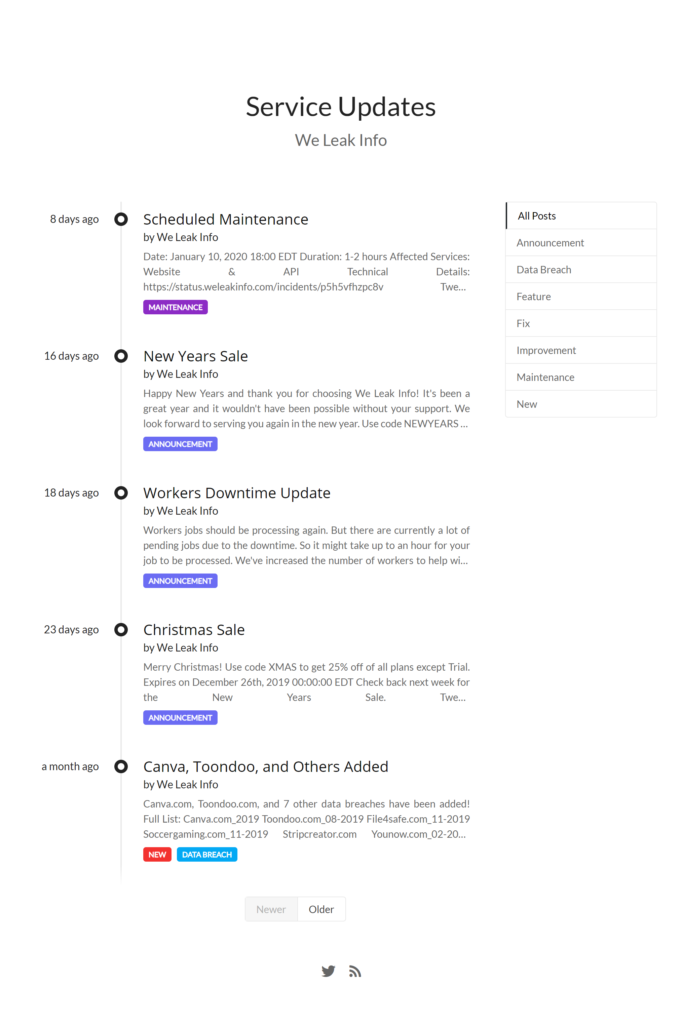
The website https://updates.weleakinfo.com is still accessible when setting the DNS record locally (151.101.1.195 updates.weleakinfo.com):
Same with https://docs.weleakinfo.com/ (35.225.27.172 docs.weleakinfo.com), it is still accessible:
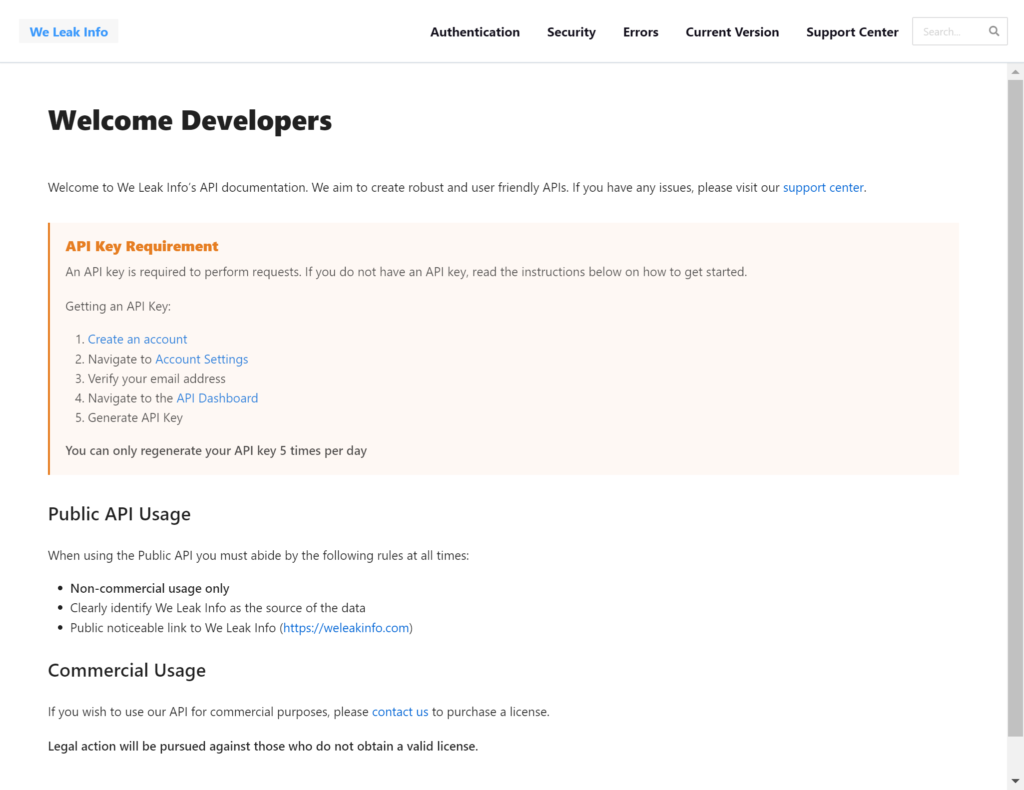
The note at the end of the docs page “Legal action will be pursued against those who do not obtain a valid license.” is almost ironic.
Same with the support page at https://support.weleakinfo.com/ (104.16.51.111 support.weleakinfo.com):
At the end of the support page it says “A subsidiary of Cyberfort Security Limited”:
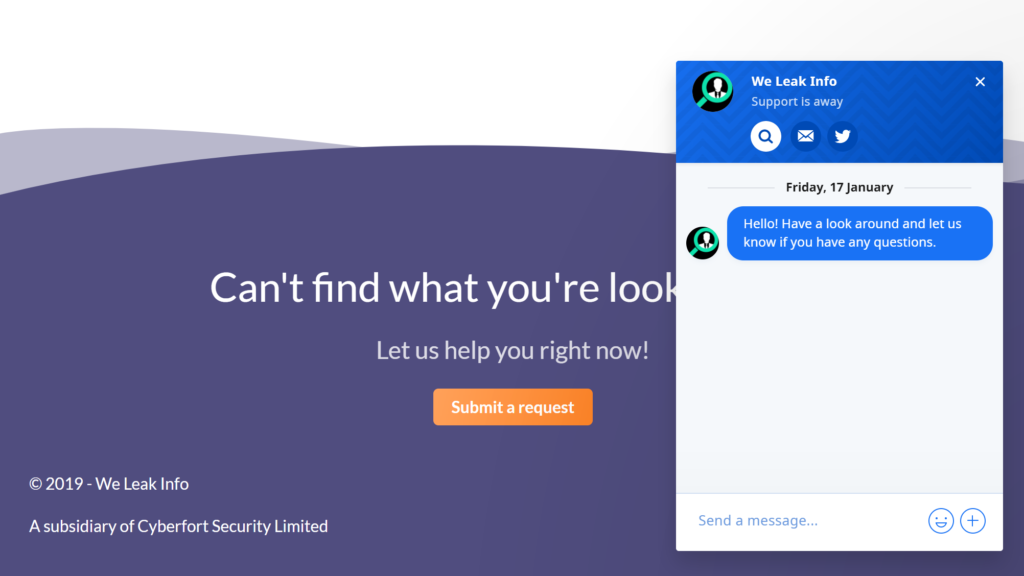
It is unclear whether “Cyberfort Security Limited” is actually owning weleakinfo, however, it is an actual company incorporated in the UK: https://beta.companieshouse.gov.uk/company/11111756
According to the filings, it was incorporated on December 14, 2017. On March 6, 2018 it was renamed to “Securefort Limited”.