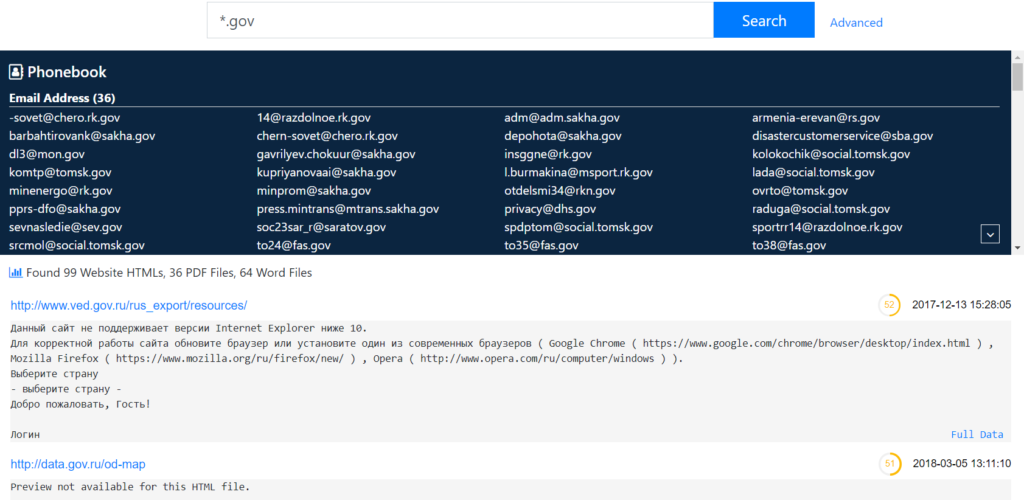
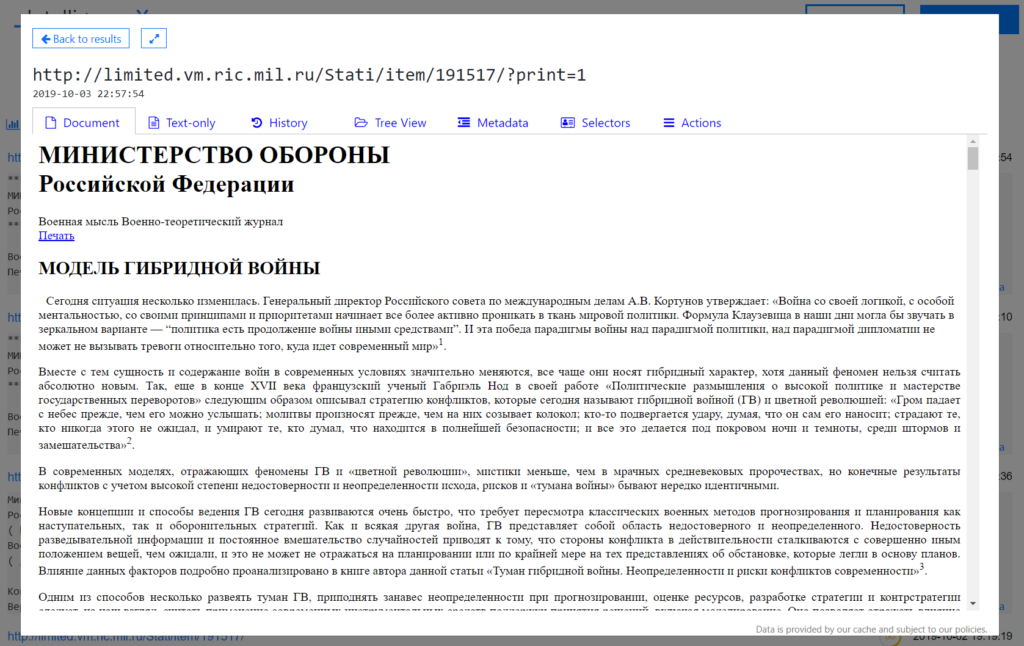
We just released a new search category “Government: Russia”. It indexes data from Russian governmental domains, including:
The historical data goes back until December 2017. That means you can go back in time and get the content of Russian governmental websites up to that point using Intelligence X.
The index contains websites, office documents such as Word files and PDF files, pictures and others. The entire dataset is 3.4 TB big and increases every day, as the crawler make daily copies. It contains 451,172,519 selectors (such as URLs, domains, email addresses, IPs, etc.) and 17,934,098 items (= unique search results).
The data is available for free on https://intelx.io – you do not even need an account.
You can select the data category in the Advanced menu, to only search the Russian government data.
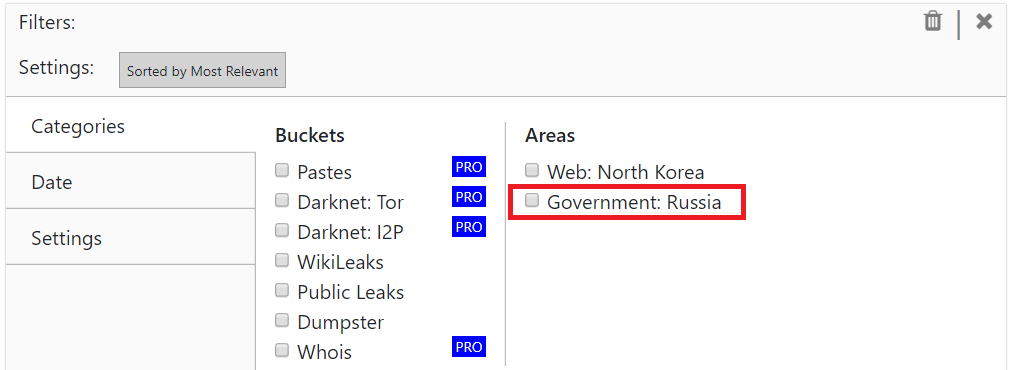
Here are real-life examples:
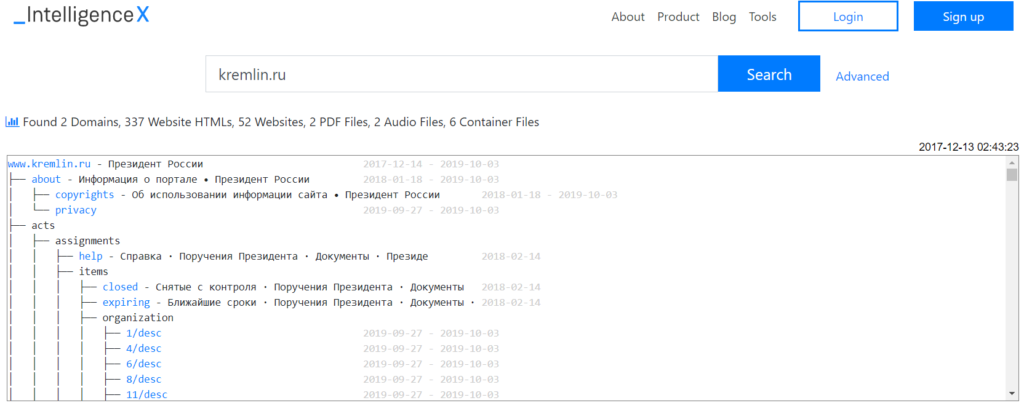
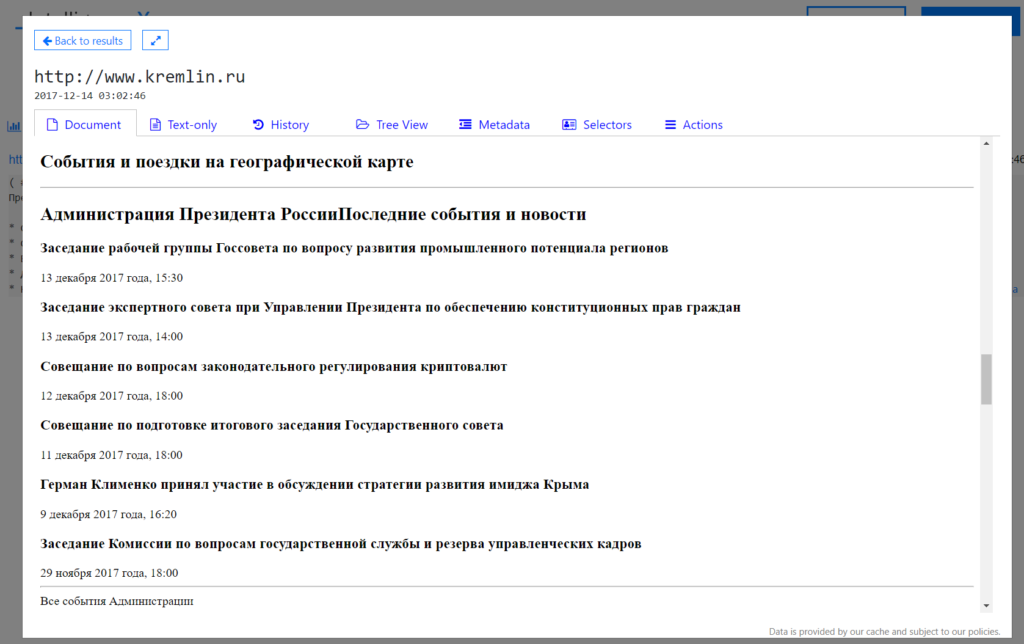
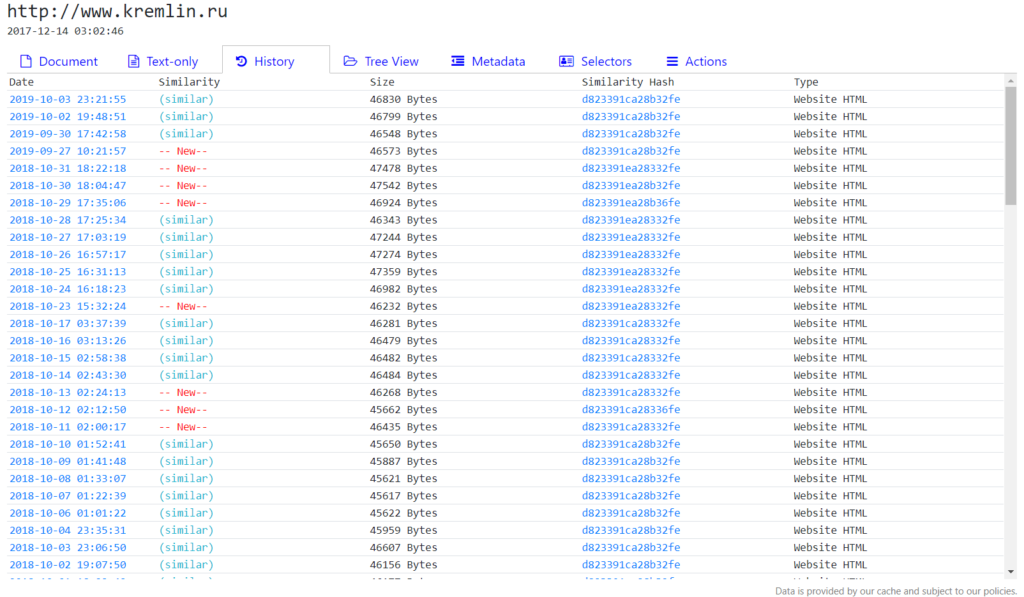
Note: There are even more fsb.ru email addresses known if you search all data across Intelligence X.