On September 19, 2019, intelx.io was under DDoS attack. 62 unique IPv4s issued 1.259.671 HTTP requests in 20 minutes.
The attack was not successful, the service continued to perform normally.
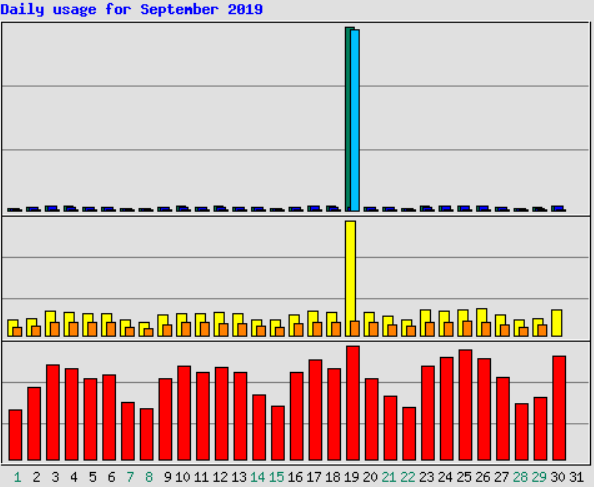
As per our Terms of Service, we reserve the right to share information about attacks with the public. This is the list of IPv4s that participated in the attack:
104.238.99.130 108.61.175.7 109.201.133.100 109.254.38.76 118.31.229.46 140.82.59.139 148.72.22.255 157.230.117.97 163.53.209.8 166.62.116.91 166.62.43.235 166.62.81.144 166.62.84.121 173.245.239.223 176.36.115.16 178.197.248.213 184.185.2.146 190.214.20.10 192.169.152.231 192.169.188.100 192.169.216.124 192.241.187.83 193.112.253.73 198.12.154.22 198.199.116.206 199.249.230.106 199.249.230.73 201.231.214.242 213.154.21.183 216.144.228.130 216.144.230.233 23.129.64.150 23.129.64.209 35.230.63.36 35.233.133.18 35.245.105.65 35.245.111.217 35.245.152.246 35.245.160.51 35.246.212.153 45.63.41.113 47.154.22.220 47.254.178.255 5.164.206.2 50.63.26.13 51.144.228.148 54.38.55.72 64.118.84.6 66.110.216.105 69.247.158.68 72.11.148.222 80.240.31.214 80.76.110.26 83.149.37.56 89.149.69.178 95.110.230.142 96.44.133.110 96.44.183.149 96.69.4.54 98.143.145.29 98.143.145.30 98.174.90.36
The attacker rotated the User Agent:
109.201.133.100 - - [19/Sep/2019:16:23:57 +0000] "GET /?9179 HTTP/1.1" 302 207 "https://www.google.com/search?q=intelx.io/" "Mozilla/5.0 (Android; Linux armv7l; rv:2.0.1) Gecko/20100101 Firefox/4.0.1 Fennec/2.0.1" 109.201.133.100 - - [19/Sep/2019:16:23:57 +0000] "GET /?15578 HTTP/1.1" 302 208 "https://www.google.com/search?q=intelx.io/" "Mozilla/5.0 (iPhone; CPU iPhone OS 11_2_2 like Mac https://m.baidu.com/mip/c/s/zhangzifan.com/wechat-user-agent.htmlOS X) AppleWebKit/604.4.7 (KHTML, like Gecko) Mobile/15C202 MicroMessenger/6.6.1 NetType/4G Language/zh_CN"