One of the file formats that does not get much attention are “.DS_Store” files, even though they might be of interest in forensic cases when analyzing hard disks or other folders (including ZIP files) from Mac machines.
“.DS_Store” is an abbreviation for “Desktop Services Store”. These files are created automatically by Apples “Finder” software (which is part of their OS). They store information about the files within a folder, including display options of folders, such as icon positions and view settings. It is a proprietary format, even though by now it is well-documented by 3rd parties. Wikipedia provides a good overview.
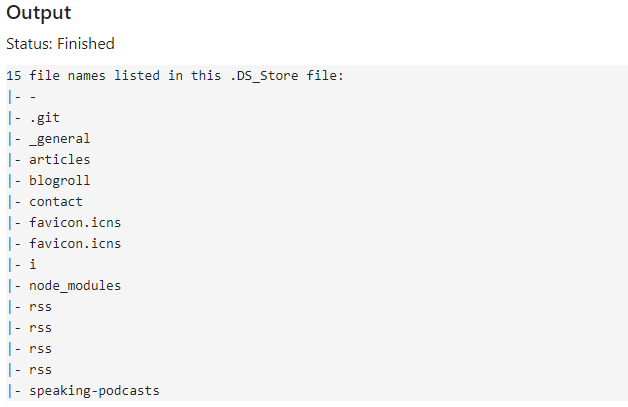
It may happen that .DS_Store files inadvertently leak filenames. If you ZIP a folder, or upload a folder to a 3rd party and then deleted individual files from that remote location, the .DS_Store might still reveal the filenames of the deleted files. Note that it does NOT leak data of the files themselves, only their names.
You can find .DS_Store files using Google Dorks or searching for them on GitHub.
You can also directly check websites by appending “.DS_Store” to the folder URL. In fact, the folks from internetwache.org analyzed the Alexa top 1 million domains (🇩🇪 German blog).
As described before, this means that some websites, thanks to .DS_Store files automatically being created, leak the list of files in their web directory, even though listing of files would be otherwise deactivated. The following screenshot is copied from the internetwache blog and shows the amount of potentially interesting files that they discovered:

Our Magic File Tool, which is part of our free OSINT toolset, is able to decode .DS_Store files and extract all filenames. Upload the file and you will immediately see the decoded result: